Abstract
Biometric authentication systems play a pivotal role in ensuring security and user convenience across diverse domains, and with technological advancements, there is a burgeoning interest in exploring emerging biometric modalities to enhance authentication effectiveness. This chapter provides a comprehensive overview of such modalities, beginning with the exploration of iris recognition as a reliable and unique biometric. The text delves into advancements like multi-sensor fusion and deep learning algorithms, addressing challenges related to occlusion and non-cooperative scenarios. The chapter introduces gait recognition as a non-intrusive biometric modality, discussing recent algorithmic advancements and challenges associated with variations in clothing, footwear, and walking speed. Behavioral biometrics, enabling continuous authentication, are explored, covering traits like keystroke dynamics, mouse dynamics, and signature dynamics. Challenges concerning user acceptance and system performance are analyzed, and techniques to enhance reliability are examined. Furthermore, the chapter delves into fusion techniques for integrating multiple biometric modalities, discussing the advantages and limitations of score-level fusion and decision-level fusion. Challenges related to interoperability, compatibility, and scalability are addressed, underscoring the importance of effective integration strategies. Privacy and security considerations are explored, with a focus on techniques such as template protection and biometric encryption to safeguard biometric data. The text also covers measures against spoofing attacks, presentation attacks, and other security vulnerabilities, emphasizing the significance of continuous research and development efforts in advancing biometric authentication systems. It stresses the need to consider privacy, security, and usability aspects while integrating emerging biometric modalities, highlighting the potential for robust and efficient authentication systems in the future through a thoughtful understanding of challenges and leveraging advancements.
Keywords
- biometric modalities
- emerging modalities
- integration challenges
- technology and algorithms
- biometric systems
1. Introduction
Biometric authentication systems have become indispensable in today’s digital landscape, offering secure and convenient means of verifying an individual’s identity. As technology continues to evolve, there is a growing interest in exploring emerging biometric modalities that can enhance the effectiveness of these systems [1]. However, the integration of these modalities poses significant challenges that must be addressed for successful implementation.
This chapter provides a comprehensive introduction to the field of emerging biometric modalities and the integration challenges associated with them. It sets the stage for understanding the potential of these modalities and the need to overcome the obstacles hindering their seamless integration.
The chapter begins by highlighting the importance of biometric authentication systems in ensuring security and user convenience across various domains, such as banking, healthcare, and access control. It emphasizes the need for continuous advancements in biometric technologies to stay ahead of evolving threats and meet the ever-increasing demands of a rapidly digitizing world.
Next, the chapter introduces the concept of emerging biometric modalities, which are new and promising techniques for capturing and analyzing unique biological or behavioral traits of individuals. These modalities offer opportunities for improved accuracy, usability, and user acceptance [2, 3, 4, 5, 6, 7, 8]. Examples of such modalities include iris recognition, gait recognition, and behavioral biometrics.
However, the integration of emerging biometric modalities into existing authentication systems presents significant challenges. These challenges range from technical considerations such as algorithmic advancements and sensor fusion techniques to practical concerns like interoperability, scalability, and system performance [9]. Overcoming these challenges requires a holistic understanding of the modalities themselves and the underlying integration processes [3, 4, 5, 6, 7, 8, 10, 11, 12, 13, 14].
Furthermore, the chapter emphasizes the importance of considering privacy and security aspects in the design and implementation of biometric authentication systems. It highlights the need to protect biometric data, ensure resistance against spoofing attacks and presentation attacks, and address potential vulnerabilities that may compromise the security of these systems.
By examining the integration challenges associated with emerging biometric modalities and highlighting the importance of privacy and security, this chapter aims to provide readers with a comprehensive understanding of the complexities involved in harnessing the potential of these modalities. It sets the stage for further exploration into specific modalities and their integration techniques, offering insights into the advancements and solutions needed to overcome the challenges faced by researchers, developers, and practitioners in the field of biometric authentication [15, 16].
This chapter provides an in-depth exploration of emerging biometric modalities and the challenges involved in integrating them into existing authentication systems. It sheds light on the potential of these modalities to enhance security and usability, while also addressing the hurdles that must be overcome for successful integration.
However, the integration of these emerging biometric modalities into existing authentication systems presents significant challenges. The chapter delves into these challenges, covering both technical and practical aspects. Technical challenges include algorithmic advancements, sensor fusion techniques, and addressing issues such as occlusion or variations in modalities. Practical challenges encompass interoperability, compatibility, scalability, and ensuring efficient system performance [3, 4, 5, 6, 7, 8, 12, 13].
Furthermore, the chapter emphasizes the critical consideration of privacy and security in the design and implementation of biometric authentication systems. It delves into the protection of biometric data, techniques for mitigating spoofing attacks and presentation attacks, and the need to address potential security vulnerabilities to safeguard the integrity and confidentiality of biometric information.
This chapter aims to equip readers with a comprehensive understanding of the complexities involved. It highlights the potential benefits of these modalities while underscoring the need to overcome technical, practical, privacy, and security challenges. This sets the stage for further exploration into specific modalities and their integration techniques, fostering advancements and solutions in the field of biometric authentication [17, 18].
1.1 Importance of continuous advancements in biometric technologies
Continuous advancements in biometric technologies are of paramount importance for several reasons [19, 20]:
Enhanced Security: As technology evolves, so do the techniques used by malicious actors to bypass security measures. Continuous advancements in biometric technologies help stay ahead of evolving threats and provide stronger defense against unauthorized access. By improving accuracy, robustness, and resistance to spoofing attacks, advancements in biometric technologies bolster the security of authentication systems.
Improved User Experience: Biometric technologies have gained popularity due to their convenience and user-friendly nature. Continuous advancements aim to enhance the user experience by improving speed, ease of use, and reliability. Faster and more accurate biometric recognition processes lead to smoother user interactions, reducing frustration and enhancing user satisfaction.
Scalability and Interoperability: Advancements in biometric technologies address challenges related to scalability and interoperability. Scalability ensures that authentication systems can handle a growing number of users efficiently without compromising performance. Interoperability enables seamless integration of biometric technologies across various platforms and systems, fostering compatibility and ease of implementation.
Mitigating False Acceptance and Rejection Rates: False acceptance (accepting an impostor) and false rejection (rejecting a legitimate user) rates are crucial factors affecting the overall performance of biometric authentication systems. Continuous advancements focus on reducing these rates through algorithmic improvements, enhanced feature extraction techniques, and better sensor capabilities. This leads to increased system accuracy and reliability.
Emerging Modalities and Applications: The advancement of biometric technologies opens doors to the exploration of emerging modalities and their applications. New biometric traits, such as iris recognition, voice recognition, or behavioral biometrics, offer unique advantages and potential use cases. Advancements in technology enable the integration and utilization of these emerging modalities, expanding the scope and capabilities of biometric authentication systems (Figure 1).
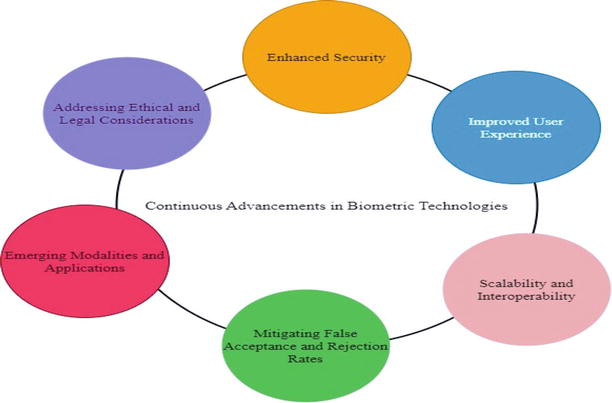
Figure 1.
Continuous advancements in biometric technologies.
In summary, continuous advancements in biometric technologies are crucial to improving security, enhancing user experience, enabling scalability and interoperability, reducing false acceptance and rejection rates, exploring emerging modalities, and addressing ethical and legal considerations. By staying at the forefront of technological progress, biometric authentication systems can meet the evolving needs and challenges of our increasingly digital world.
Addressing challenges in biometric authentication systems shown in the Figure 2, it is crucial for improving security, enhancing usability, fostering user trust and acceptance, ensuring compliance, accommodating diverse user needs, and future-proofing technology. By striving to overcome these challenges, organizations can unlock the full potential of biometric systems, delivering robust and user-friendly authentication solutions in an increasingly digital world.
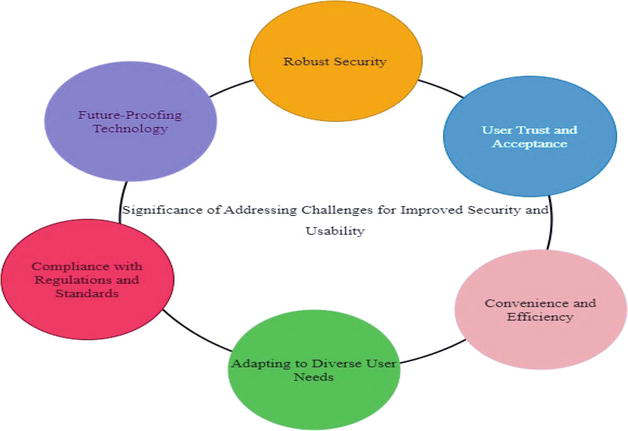
Figure 2.
Addressing challenges for improved security and usability.
2. Iris recognition
In the realm of biometric authentication, iris recognition has emerged as a highly reliable and unique modality that offers significant advantages over other biometric traits. The human iris, with its intricate and distinct patterns, provides a powerful means of identification and verification [21]. This introduction sheds light on the reliability and uniqueness of iris recognition as a biometric modality.
Iris recognition technology involves capturing and analyzing the patterns present in the iris, which is the colored portion of the eye surrounding the pupil. The unique patterns within the iris, such as crypts, furrows, and ridges, exhibit a high degree of variation among individuals, making it an ideal candidate for reliable and accurate identification [3, 4, 5, 6, 7, 8, 22, 23].
One of the primary reasons for the reliability of iris recognition lies in the stability of the iris patterns. Unlike other biometric traits such as fingerprints, which can be subject to wear, damage, or alteration, the iris remains relatively stable throughout a person’s lifetime. This stability ensures that the iris patterns used for identification purposes remain consistent over extended periods, leading to reliable and consistent recognition outcomes.
Furthermore, the level of uniqueness offered by the iris as a biometric modality is unparalleled. The probability of two individuals having identical iris patterns is extraordinarily low, estimated to be as low as one in several billion. This high level of uniqueness enhances the effectiveness of iris recognition systems in accurately distinguishing between individuals, minimizing the chances of false matches or false rejections.
Iris recognition technology has witnessed significant advancements over the years, with the introduction of robust algorithms, high-resolution imaging devices, and multi-sensor fusion techniques [3, 4, 5, 6, 7, 8, 24]. These advancements have further enhanced the accuracy and reliability of iris recognition systems, enabling fast and precise identification in various applications.
Moreover, iris recognition boasts several advantages that contribute to its reliability and uniqueness as a biometric modality. It is a non-intrusive technique that does not require physical contact, making it more hygienic and user-friendly compared to other modalities. Additionally, the iris is highly resistant to forgery or spoofing attempts, as it cannot be easily replicated or manipulated, further enhancing the security of iris recognition systems.
Iris recognition stands out as a reliable and unique biometric modality due to the stability of iris patterns, the high level of uniqueness among individuals, and the advancements in iris recognition technology [25]. Its reliability, non-intrusiveness, and resistance to forgery make it an ideal choice for a wide range of applications, including access control, border control, and identity verification. With continuous advancements, iris recognition continues to shape the landscape of biometric authentication, offering a highly accurate and secure means of personal identification.
2.1 Advancements in iris recognition techniques
Advancements in iris recognition techniques have significantly contributed to the improvement of accuracy, speed, and usability of iris recognition systems. These advancements encompass various aspects of iris recognition technology and have been driven by advancements in image processing, machine learning, and hardware capabilities [26, 27]. Here are some notable advancements in iris recognition techniques:
High-resolution Imaging: The introduction of high-resolution iris imaging devices has played a pivotal role in improving the quality of iris images captured for recognition purposes. High-resolution sensors allow for finer details and more precise extraction of iris patterns, resulting in enhanced accuracy and reliability.
Robust Feature Extraction: Feature extraction algorithms have undergone significant advancements to better capture and represent the unique patterns within the iris. Various techniques, such as Daugman’s rubber sheet model, have been refined to extract robust iris features effectively. These algorithms are designed to handle variations in iris images caused by factors such as illumination changes, occlusions, and pupil dilation, ensuring reliable recognition performance.
Template Compression and Storage: With the growing need for efficient storage and transmission of biometric templates, advancements have been made in iris template compression techniques. These techniques reduce the size of the iris templates while preserving essential information, allowing for faster matching and improved system efficiency.
Multi-Sensor Fusion: Multi-sensor fusion techniques involve combining information from multiple biometric sensors to enhance the accuracy and reliability of iris recognition systems. For example, combining iris recognition with other modalities such as face recognition or periocular recognition can provide more robust identification results, particularly in challenging scenarios such as low-quality images or occlusions.
Deep Learning Approaches: Deep learning algorithms, specifically convolutional neural networks (CNNs), have been applied to iris recognition tasks with promising results. These algorithms can automatically learn discriminative features from iris images and achieve state-of-the-art recognition performance. Deep learning techniques have also contributed to improved robustness against presentation attacks and increased resistance to spoofing attempts.
Real-Time and Mobile Applications: Advancements in hardware capabilities, such as the availability of powerful processors and specialized hardware accelerators, have enabled real-time iris recognition on mobile devices. This development has opened opportunities for secure and convenient iris-based authentication in mobile applications, including smartphones and tablets.
Cross-Dataset Generalization: Generalization across different datasets is crucial to ensure the effectiveness of iris recognition systems in real-world scenarios. Advancements in cross-dataset generalization techniques enable iris recognition models to perform well on unseen or challenging datasets, enhancing the system’s usability and versatility (Figure 3).
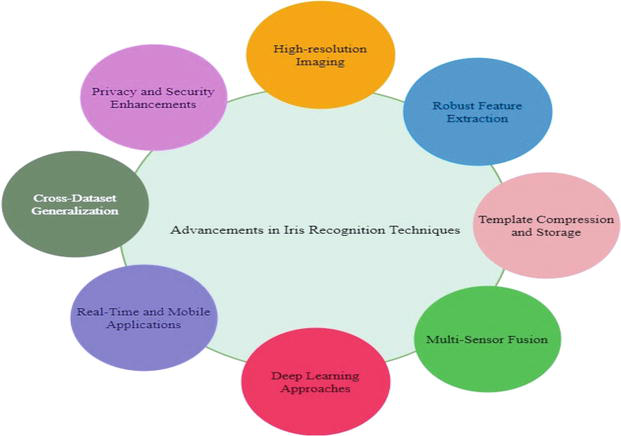
Figure 3.
Advancements in iris recognition techniques.
These advancements collectively contribute to the continuous improvement of iris recognition techniques, making them more accurate, reliable, and suitable for a wide range of applications. By leveraging advancements in imaging technology, feature extraction algorithms, multi-sensor fusion, deep learning, real-time processing, and privacy-enhancing techniques, iris recognition systems are poised to deliver robust and secure biometric authentication solutions in various domains.
2.2 Multi-sensor fusion for enhanced accuracy and robustness
Multi-sensor fusion techniques in biometric authentication systems involve combining information from multiple biometric sensors to enhance accuracy, robustness, and reliability [28]. By integrating data from different modalities, multi-sensor fusion offers several benefits that surpass the limitations of using a single sensor [3, 4, 5, 6, 7, 8, 10, 29]. Here are key advantages and advancements related to multi-sensor fusion for enhanced accuracy and robustness:
Improved Recognition Performance: Combining data from multiple sensors allows for the extraction of complementary information from different biometric modalities. This fusion of modalities can enhance recognition performance by mitigating the limitations of individual sensors. For example, while iris recognition provides high accuracy, combining it with face recognition or periocular recognition can enhance robustness against occlusions, variations in pose, or low-quality images.
Increased Resistance to Spoofing Attacks: Multi-sensor fusion helps improve the system’s resilience against spoofing attacks, where individuals attempt to deceive the system by using fake biometric samples. By combining multiple modalities with different vulnerabilities to spoofing, the system becomes more resistant to presentation attacks. For instance, combining iris recognition with fingerprint or voice recognition reduces the risk of successful spoofing attempts.
Enhanced Usability and User Experience: Multi-sensor fusion can improve system usability by accommodating diverse user populations and scenarios. Certain biometric modalities may be less effective for specific individuals due to factors such as injuries, disabilities, or physiological variations. By incorporating multiple sensors, the system can adapt to different user characteristics and provide a more inclusive and user-friendly authentication experience.
Robustness against Variability and Noise: Biometric modalities can exhibit variations due to factors like illumination changes, pose variations, or sensor noise. Multi-sensor fusion can help mitigate these variations by combining data from sensors that capture different aspects of the same biometric trait. By leveraging the strengths of each sensor, the system becomes more robust against variability and noise, leading to improved recognition accuracy.
Reliable Decision Making: Multi-sensor fusion enables the system to make more reliable and informed decisions by considering multiple sources of information. Fusion algorithms can employ voting mechanisms, weighted averaging, or machine learning techniques to integrate the outputs from different sensors and arrive at a more accurate and confident decision. This reduces the likelihood of false matches or false rejections, improving the overall reliability of the system (Figure 4).
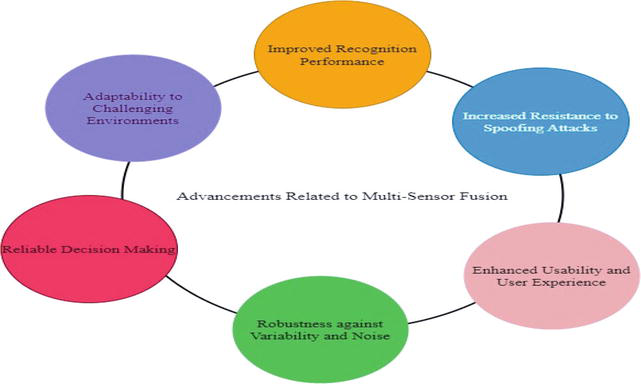
Figure 4.
Advancements related to multi-sensor fusion.
Advancements in multi-sensor fusion techniques involve the development of sophisticated algorithms for data fusion, feature extraction, decision fusion, and learning-based approaches. These advancements leverage machine learning, statistical modeling, and pattern recognition techniques to extract valuable information from multiple sensors and achieve improved accuracy, robustness, and usability in biometric authentication systems.
In conclusion, multi-sensor fusion offers substantial benefits for biometric authentication systems by combining information from multiple sensors. The integration of data from different modalities leads to enhanced accuracy, increased resistance to spoofing attacks, improved usability, robustness against variability and noise, reliable decision making, and adaptability to challenging environments. With ongoing advancements in fusion algorithms and sensor technologies, multi-sensor fusion continues to play a vital role in advancing the performance and reliability of biometric authentication systems [12, 13, 30, 31].
2.3 Deep learning algorithms for improved iris feature extraction and matching
Deep learning algorithms have revolutionized iris recognition by significantly improving iris feature extraction and matching processes. These algorithms, particularly convolutional neural networks (CNNs), have demonstrated remarkable capabilities in learning discriminative features directly from iris images, leading to enhanced accuracy and robustness in iris recognition systems [32, 33]. Here are key aspects highlighting the contributions of deep learning algorithms in iris feature extraction and matching:
End-to-End Feature Learning: Deep learning algorithms enable end-to-end feature learning, eliminating the need for handcrafted feature extraction techniques. CNNs can automatically learn hierarchical representations of iris images, capturing complex patterns and discriminative features directly from the raw input data. This ability to learn features directly from iris images has proven highly effective in improving recognition performance.
Robust Feature Extraction: Deep learning algorithms can extract robust and discriminative features from iris images, even in the presence of variations caused by factors such as occlusions, noise, pose variations, and changes in lighting conditions. By leveraging the power of CNNs, these algorithms can learn invariant representations that are less sensitive to such variations, resulting in more accurate and reliable feature extraction.
Improved Generalization: Deep learning algorithms excel in generalizing learned representations to unseen or challenging datasets. The hierarchical nature of CNNs allows them to capture both low-level and high-level features, enabling better generalization across different individuals, image qualities, and imaging devices. This capability enhances the adaptability and robustness of iris recognition systems, making them more effective in real-world scenarios.
Enhanced Matching Accuracy: Deep learning algorithms have demonstrated improved matching accuracy in iris recognition. By extracting highly discriminative features, CNNs enable more precise matching of iris patterns, reducing the risk of false matches or false rejections. The learned features capture subtle variations in the iris, making the matching process more accurate and reliable.
Fusion with Other Modalities: Deep learning algorithms also facilitate the fusion of iris recognition with other modalities, such as face recognition or periocular recognition. By employing multimodal deep learning architectures, the system can leverage the strengths of each modality to improve overall recognition performance. This fusion of modalities enhances the system’s ability to handle challenging scenarios and increases the robustness of the authentication process.
Transfer Learning and Fine-tuning: Deep learning algorithms benefit from transfer learning and fine-tuning techniques, which allow models trained on large-scale datasets to be adapted to specific iris recognition tasks. Pre-trained CNN models, such as those trained on large image databases like ImageNet, can be utilized as a starting point for iris recognition tasks. Fine-tuning the pre-trained models on iris-specific datasets enhances their performance and accelerates the training process.
In deep learning algorithms have revolutionized iris recognition by enabling end-to-end feature learning, robust feature extraction, improved generalization, enhanced matching accuracy, fusion with other modalities, and efficient model compression. With their ability to automatically learn discriminative features from iris images, deep learning algorithms have significantly advanced the state-of-the-art in iris recognition systems, paving the way for more accurate and reliable biometric authentication solutions.
Iris recognition, despite its many advantages, also faces several challenges that need to be addressed for the successful deployment and widespread adoption of iris recognition systems . The challenges of iris recognition are shown in the Figure 5.
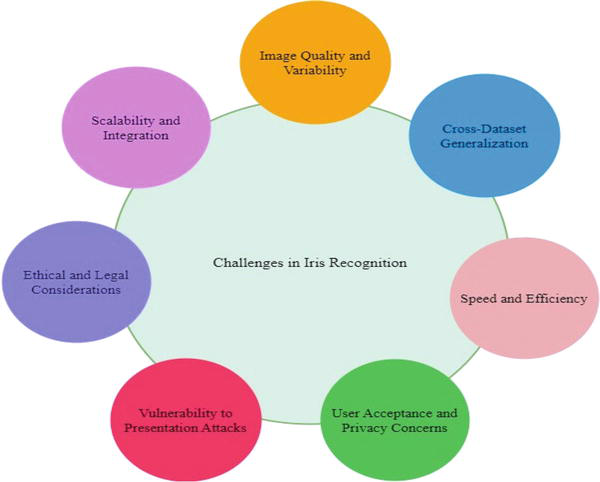
Figure 5.
Challenges in iris recognition.
Addressing these challenges requires ongoing research and development efforts, collaboration between academia and industry, and continuous advancements in algorithms, hardware technologies, and standardization efforts. By overcoming these challenges, iris recognition systems can fulfill their potential as reliable, secure, and widely adopted biometric authentication solutions.
2.4 Handling non-cooperative scenarios and ensuring accurate recognition
Non-cooperative scenarios in iris recognition refer to situations where individuals may not fully cooperate or adhere to specific image capture requirements, leading to challenges in acquiring high-quality iris images [34]. Ensuring accurate recognition in such scenarios requires the implementation of various techniques and strategies. Here are some approaches commonly employed to handle non-cooperative scenarios and enhance recognition accuracy:
Robust Image Acquisition: Non-cooperative scenarios often involve individuals who may have difficulty positioning their eyes correctly or maintaining a steady gaze during image capture. Robust image acquisition techniques can be used to guide the individual and ensure proper alignment and focus. This may involve providing real-time feedback, visual cues, or audio instructions to assist the person in positioning their eyes correctly for image capture.
Multiple Image Acquisition: Capturing multiple iris images from different angles, under varying lighting conditions, or using different wavelengths can increase the likelihood of obtaining clear and usable iris samples. By acquiring a diverse set of images, the system can improve the chances of capturing an iris image with sufficient quality for accurate recognition. Multiple images can also be used for fusion or selection purposes to enhance recognition accuracy.
Adaptive Feature Extraction: Non-cooperative scenarios can introduce variability in iris appearance, such as changes in pupil dilation, eyelid position, or iris texture. Adaptive feature extraction techniques that can adapt to such variations are crucial. These techniques should be able to extract robust features from different types of iris images, including those with partial occlusions or variations caused by non-compliance.
Quality Assessment and Rejection: Implementing quality assessment mechanisms can help identify and reject low-quality iris images. Quality assessment algorithms analyze various aspects of the iris image, such as focus, illumination, and iris coverage, to determine its suitability for recognition. By rejecting poor-quality images, the system can focus on processing only reliable and accurate iris samples, improving recognition performance.
Anti-Spoofing Techniques: Non-cooperative scenarios may also be susceptible to presentation attacks, where individuals attempt to deceive the system using fake or altered iris samples. Robust anti-spoofing techniques can help detect and reject such attacks, ensuring the authenticity of the captured iris samples. Anti-spoofing methods may utilize texture analysis, motion detection, or multi-modal fusion to differentiate between genuine and spoofed iris patterns.
User Education and Awareness: Educating users about the importance of cooperation and following image capture instructions can significantly improve the quality of acquired iris images. Increasing user awareness about the benefits and proper usage of iris recognition systems can encourage cooperation and enhance recognition accuracy in non-cooperative scenarios (Figure 6).
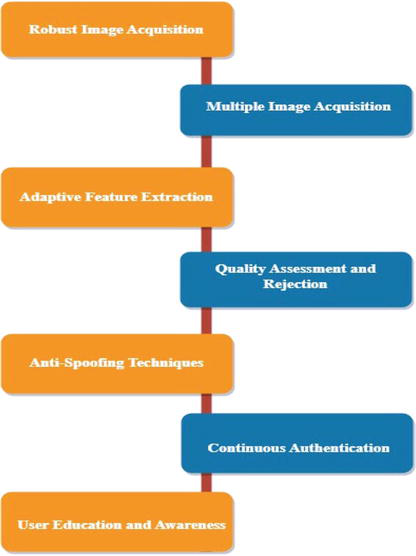
Figure 6.
Handling non-cooperative scenarios and ensuring accurate recognition.
Addressing non-cooperative scenarios requires a combination of technical advancements, user education, and system design considerations. By implementing robust image acquisition techniques, adaptive feature extraction algorithms, quality assessment mechanisms, anti-spoofing techniques, and continuous authentication, iris recognition systems can handle non-cooperative scenarios more effectively and ensure accurate recognition in real-world environments [29, 35].
3. Gait recognition
Gait recognition is a non-intrusive biometric modality that involves the analysis and identification of an individual’s walking pattern [36]. Just like other biometric modalities such as fingerprint or iris recognition, gait recognition relies on the uniqueness and distinctiveness of an individual’s gait as a means of identification. Gait recognition offers several advantages over other biometric modalities, primarily because it can be performed from a distance without requiring any physical contact or cooperation from the individuals being recognized.
The human gait is influenced by various factors such as body structure, skeletal proportions, muscle movements, and individual walking style. These characteristics create a unique and identifiable walking pattern for each individual, which can be captured and analyzed for biometric recognition purposes. Gait recognition systems typically utilize video surveillance cameras or motion sensors to capture the walking patterns of individuals in real-time or from recorded video footage.
Gait recognition has gained considerable attention in recent years due to its non-intrusive nature and potential applications in security and surveillance, forensic investigations, and access control systems. It offers advantages in scenarios where traditional biometric modalities may not be feasible or practical, such as in surveillance applications where individuals need to be recognized from a distance without their knowledge [2].
One of the significant advantages of gait recognition is its potential for continuous and unobtrusive identification. Unlike other biometric modalities that require individuals to actively present their biometric samples, gait recognition can be performed covertly by analyzing an individual’s walking pattern in a passive manner. This makes it particularly useful in scenarios where continuous monitoring and identification are desired, such as in crowded public areas or high-security environments.
In addition to its non-intrusive nature, gait recognition also offers other benefits, including its resilience to changes in appearance, as gait patterns can be recognized even if the individual’s appearance changes through variations in clothing or other external factors. Gait recognition can also complement other biometric modalities by providing an additional layer of identification or authentication, enhancing overall security and accuracy [37].
However, gait recognition also presents its own set of challenges. Variations in walking conditions, such as footwear, walking speed, terrain, and viewpoint changes, can affect the accuracy of gait recognition systems. Furthermore, the performance of gait recognition can be influenced by factors such as age, injuries, or physical disabilities that may impact an individual’s gait pattern. Overcoming these challenges requires the development of robust algorithms that can handle variations in gait patterns and adapt to different walking conditions.
In conclusion, gait recognition offers a non-intrusive and continuous means of identifying individuals based on their walking patterns. Its potential applications in security, surveillance, and access control make it an attractive biometric modality. While challenges exist, ongoing research and advancements in gait recognition algorithms continue to improve the accuracy and reliability of this unique and non-intrusive biometric technology.
3.1 Deep learning approaches for improved gait analysis and identification
Deep learning approaches have significantly advanced gait analysis and identification by leveraging the power of neural networks to automatically learn discriminative features from gait data [38]. These approaches have demonstrated superior performance in capturing the complex dynamics of gait patterns and improving the accuracy and robustness of gait recognition systems. Here are some deep learning approaches used for improved gait analysis and identification:
Convolutional Neural Networks (CNNs): CNNs have been widely employed for gait analysis tasks, particularly for gait feature extraction from gait images or video frames. These networks can automatically learn hierarchical representations of gait features by utilizing convolutional layers, which capture spatial patterns and local correlations in gait images. CNNs have shown improved accuracy in gait recognition, especially when dealing with variations in pose, viewpoint, and appearance.
Recurrent Neural Networks (RNNs): RNNs have proven effective in modeling the temporal dynamics of gait patterns. By processing gait sequences in a sequential manner, RNNs, such as Long Short-Term Memory (LSTM) networks, can capture the temporal dependencies and variations in gait patterns over time. RNNs have been used for gait feature extraction and recognition tasks, enhancing the performance of gait recognition systems by considering the dynamic nature of gait.
Siamese Networks: Siamese networks are commonly used for gait verification or similarity learning tasks. These networks consist of two identical sub-networks sharing the same weights, where each sub-network processes a different gait image or sequence. Siamese networks learn to map gait samples into a feature space where similarity or dissimilarity can be measured. This approach has been used for gait-based person verification and identification, facilitating robust and accurate gait matching.
Generative Adversarial Networks (GANs): GANs have been employed for gait-related tasks, including gait synthesis and augmentation. GANs can generate realistic synthetic gait samples that resemble real gait patterns, contributing to the augmentation of gait datasets and addressing the challenge of limited labeled data. GANs have also been used in gait anti-spoofing, generating synthetic spoofed gait samples for training anti-spoofing models, leading to improved system security.
These deep learning approaches have shown great potential in improving gait analysis and identification. They have demonstrated superior performance in capturing the complex dynamics of gait patterns, handling variations in pose, viewpoint, and appearance, and enhancing the robustness and accuracy of gait recognition systems. Continued research and advancements in deep learning algorithms will further contribute to the advancement of gait analysis and identification techniques.
3.2 Challenges in gait recognition
While gait recognition offers promising advantages as a non-intrusive biometric modality, it also faces several challenges that need to be addressed for practical and reliable deployment [39]. Some of the key challenges in gait recognition include:
Variability in Walking Conditions: Gait patterns can be influenced by various factors such as walking speed, footwear, terrain, and carrying objects. These variations introduce challenges in capturing and analyzing consistent gait features across different conditions. Robust algorithms are needed to handle these variations and ensure accurate recognition in real-world scenarios.
Viewpoint and Pose Variations: Gait recognition systems need to be robust to changes in viewpoint and pose. Different camera angles or perspectives can significantly affect the appearance of gait patterns, making it challenging to match and identify individuals accurately. Developing algorithms that can handle variations in viewpoint and pose is crucial for reliable gait recognition.
Covariate Factors: Gait patterns can be affected by covariate factors such as age, weight, clothing, and health conditions. These factors introduce intra-class variations and can impact the accuracy of gait recognition systems. Robust feature extraction and normalization techniques are necessary to handle these covariate factors and ensure accurate identification.
Limited Training Data: Deep learning algorithms used in gait recognition often require large amounts of labeled training data to learn representative gait features. However, collecting large-scale gait datasets with sufficient labeled samples can be challenging. Limited training data can lead to overfitting or reduced generalization performance. Developing effective techniques for data augmentation and transfer learning can help alleviate this challenge.
Data Privacy and Ethics: Gait recognition systems raise concerns regarding privacy and ethics. Gait data can reveal sensitive information about individuals, and there is a need to protect the privacy and rights of individuals during data collection, storage, and usage. Ensuring secure and responsible deployment of gait recognition systems is crucial to address these privacy and ethical concerns (Figure 7).
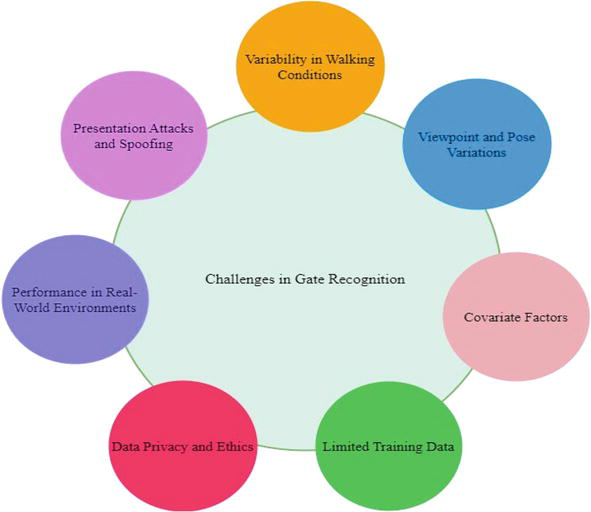
Figure 7.
Challenges in gait recognition.
Addressing these challenges requires interdisciplinary research efforts encompassing computer vision, machine learning, and biometrics. Robust algorithms that can handle variations in walking conditions, viewpoint changes, and covariate factors, along with advancements in data collection and privacy protection, will contribute to the development of more accurate and reliable gait recognition systems. Additionally, addressing the ethical implications and ensuring the systems’ performance in real-world environments will further enhance the practicality and trustworthiness of gait recognition technology.
3.3 Techniques to address challenges and improve recognition accuracy
To address the challenges and improve recognition accuracy in biometric systems, including gait recognition, several techniques and approaches can be employed [40]. Here are some effective techniques:
Multi-Sensor Fusion: Integrating data from multiple sensors can enhance recognition accuracy. For gait recognition, combining information from different sensors such as cameras, accelerometers, or pressure sensors can provide a more comprehensive representation of gait patterns. Fusion techniques can be applied at the feature level or decision level to leverage the complementary information and improve recognition performance.
Feature Selection and Dimensionality Reduction: Gait data often contain high-dimensional feature vectors, which can lead to increased computational complexity and potential overfitting. Feature selection methods, such as statistical analysis or machine learning-based approaches, can help identify the most relevant and discriminative features for gait recognition. Additionally, dimensionality reduction techniques like Principal Component Analysis (PCA) or Linear Discriminant Analysis (LDA) can reduce the feature space dimension and improve computational efficiency.
Adaptive and Personalized Models: Recognizing that gait patterns can vary across individuals, adapting the models to individual characteristics can improve accuracy. Personalized models can be trained for each user to capture their specific gait dynamics, leading to better recognition performance. Adaptive models can also dynamically update and adjust their parameters based on user-specific changes over time, ensuring robust and up-to-date recognition.
Ensemble Methods: Ensemble methods combine multiple classifiers or models to make collective decisions. By aggregating the predictions of diverse models, ensemble methods can improve the robustness and accuracy of the recognition system. Techniques such as bagging, boosting, or stacking can be applied to create an ensemble of gait recognition models and achieve better performance.
Robust Feature Extraction: Gait features extraction plays a crucial role in recognition accuracy. Developing robust feature extraction techniques that are invariant to variations such as clothing, footwear, or walking speed is essential. Advanced feature extraction methods, including deep learning-based approaches, can automatically learn discriminative features from gait data, leading to improved recognition accuracy.
By applying these techniques, gait recognition systems can overcome challenges, enhance recognition accuracy, and provide reliable and secure biometric authentication. It is important to consider the specific requirements and constraints of the application domain while selecting and implementing these techniques.
4. Behavioral biometrics
Behavioral biometrics refers to the use of unique behavioral characteristics and patterns exhibited by individuals for the purpose of continuous authentication. Unlike static biometric traits such as fingerprints or iris patterns, behavioral biometrics focus on the analysis of dynamic and continuously evolving behavioral patterns. This approach provides an additional layer of security by continuously monitoring and verifying the user’s identity based on their unique behavioral traits.
Behavioral biometrics encompass a wide range of human activities, including typing patterns, mouse movements, gesture recognition, voice characteristics, walking gait, and even cognitive behavior [41]. These behavioral traits are highly personalized and difficult to mimic, making them suitable for continuous authentication in various applications such as online banking, access control systems, and mobile device security.
The concept of behavioral biometrics revolves around the idea that individuals exhibit consistent patterns and nuances in their behaviors over time [9]. By capturing and analyzing these behavioral patterns, algorithms can create user-specific models that establish a baseline of normal behavior. Continuous monitoring and analysis of the user’s ongoing behavior allow for real-time authentication and detection of any deviations from the established patterns, which may indicate unauthorized access or identity theft attempts [42].
One of the key advantages of behavioral biometrics is its non-intrusive nature. Unlike traditional biometric methods that require explicit actions or physical contact, behavioral biometrics can be seamlessly integrated into users’ natural activities without requiring any additional effort. This makes it convenient and user-friendly, enabling continuous authentication without causing disruptions or inconvenience to the user.
However, behavioral biometrics also present some challenges. Variations in behavior due to external factors like environmental conditions or temporary physical conditions can affect the accuracy of recognition systems. Additionally, the dynamic nature of behavioral traits requires adaptive and robust algorithms that can effectively handle variations and changes over time.
Behavioral biometrics offers a promising approach for continuous authentication, providing an additional layer of security beyond traditional biometric methods. By leveraging the unique behavioral characteristics exhibited by individuals, it enables continuous monitoring and verification of user identity in real-time, contributing to enhanced security and protection against unauthorized access.
4.1 Various behavioral biometric traits
Behavioral biometrics encompass a wide range of human activities and traits that can be utilized for continuous authentication [43]. Here are some of the commonly used behavioral biometric traits:
Typing Patterns: The way individuals type on a keyboard, including keystroke dynamics such as key press duration, key hold time, and time intervals between keystrokes, can be used as a behavioral biometric trait.
Mouse Movements: The movement patterns of a mouse or trackpad, including speed, acceleration, and trajectory, can be analyzed for behavioral biometrics.
Gesture Recognition: The unique way individuals perform gestures, such as swiping, tapping, or pinching on touchscreens or touchpads, can be utilized for behavioral authentication.
Voice Characteristics: The characteristics of an individual’s voice, including pitch, tone, rhythm, and pronunciation, can serve as behavioral biometric traits.
Signature Dynamics: The way individuals sign their name, including signature speed, pressure, stroke order, and pen angle, can be used as a behavioral biometric trait.
Walking Gait: The unique walking style and gait dynamics, including stride length, cadence, and body movements, can be analyzed for behavioral biometric recognition.
Handwriting Patterns: The way individuals write, including pen pressure, stroke order, letter shapes, and spacing, can be used as a behavioral biometric trait.
Eye Movement: The patterns of eye movements, such as fixations, saccades, and gaze duration, can be utilized as a behavioral biometric trait.
These are just a few examples of behavioral biometric traits that can be used for continuous authentication. The selection of specific traits depends on the application, user interaction methods, and available data for analysis. By leveraging the unique characteristics exhibited in these behavioral traits, systems can establish user-specific behavioral profiles for continuous authentication and detect any anomalies or unauthorized access attempts in real-time.
4.2 Challenges in behavioral biometrics
While behavioral biometrics offer several advantages for continuous authentication, they also face certain challenges that need to be addressed [44, 45]. Here are some of the key challenges in behavioral biometrics:
Variability and Contextual Dependencies: Behavioral biometric traits can be influenced by various factors such as environmental conditions, device characteristics, user state, and task context. Variability in behavioral patterns due to these factors can impact the accuracy and reliability of recognition systems. Robust algorithms need to be developed to handle such variations and account for contextual dependencies [46].
User Acceptance and Privacy Concerns: Behavioral biometric systems rely on capturing and analyzing users’ personal behaviors, which may raise privacy concerns. Users may be hesitant to provide continuous access to their behavioral data, fearing misuse or surveillance. Balancing the need for security with user privacy and obtaining user acceptance for behavioral biometrics is a challenge that needs to be addressed.
Spoofing and Impersonation Attacks: Behavioral biometric traits can be vulnerable to spoofing attacks, where attackers attempt to mimic or replicate the behavioral patterns of legitimate users. Adversaries may study the behavioral traits or employ techniques to deceive the recognition systems. Developing robust anti-spoofing techniques and ensuring the systems can distinguish between genuine user behavior and fraudulent attempts is a critical challenge.
Intra-class Variability: Even within the same individual, behavioral biometric traits may exhibit variations over time. Factors such as fatigue, emotional state, or physical conditions can affect behavioral patterns, leading to intra-class variability. Algorithms need to account for these variations and maintain accuracy in recognizing an individual’s genuine behavior while accommodating natural changes.
Sample Size and Imbalanced Datasets: Behavioral biometric systems require sufficient data samples for training and validation. Obtaining large and diverse datasets can be challenging, particularly for less common or emerging behavioral traits. Imbalanced datasets, where some users have significantly more data samples than others, can affect the fairness and performance of recognition systems. Techniques to address these challenges include data augmentation, transfer learning, and handling class imbalance during model training (Figure 8).
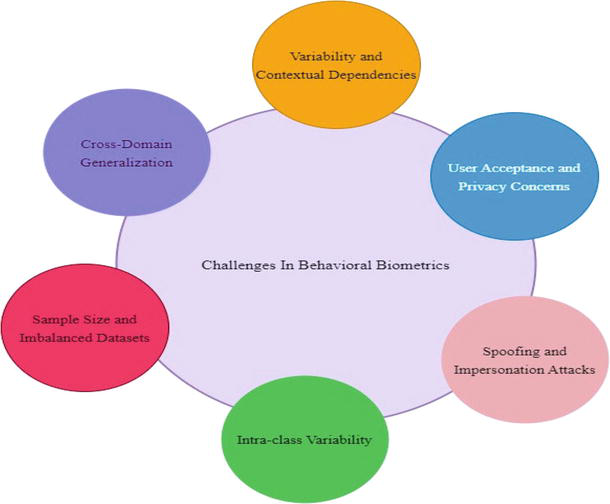
Figure 8.
Challenges in behavioral biometrics.
Addressing these challenges in behavioral biometrics requires advancements in algorithm design, data collection strategies, anti-spoofing techniques, user-centric approaches, and privacy-preserving mechanisms. Overcoming these challenges will contribute to the development of more robust and reliable behavioral biometric systems for continuous authentication in various applications [12, 13].
4.3 User acceptance and system performance
User acceptance and system performance are two critical aspects that need to be considered in the development and deployment of behavioral biometric systems [47]. Let us discuss each of these factors in more detail:
User Acceptance: User acceptance refers to the willingness of individuals to adopt and use behavioral biometric systems. The success of any biometric system relies on user cooperation and their willingness to provide their behavioral data for authentication purposes. Several factors influence user acceptance:
Privacy Concerns: Users may have concerns about their personal information and behavior being monitored or stored. It is important to address these concerns by implementing strong privacy policies, data protection measures, and transparent communication regarding the purpose and use of the collected behavioral data.
Perceived Security: Users need to be assured that the behavioral biometric system is secure and reliable. Clear communication about the security measures in place, encryption techniques, and robustness against attacks can help build trust and enhance user acceptance.
User Experience: The usability and convenience of the system play a crucial role in user acceptance. The system should be user-friendly, intuitive, and have a seamless integration into existing workflows. Users should perceive the behavioral biometric authentication process as efficient and less burdensome compared to traditional authentication methods.
System Performance: System performance refers to the accuracy, reliability, and efficiency of the behavioral biometric system [48]. Key factors that influence system performance include:
Accuracy and False Acceptance/Rejection Rates: The system should achieve a high level of accuracy in distinguishing between genuine users and impostors while maintaining low false acceptance and rejection rates. A balance needs to be struck to ensure both security and usability.
Robustness: The system should be robust against variations in behavior due to contextual factors, user conditions, or device differences. It should be able to accommodate natural changes in behavior while maintaining accurate recognition.
Speed and Responsiveness: The system should provide fast and responsive authentication to ensure a seamless user experience. Lengthy authentication processes or delays can negatively impact user acceptance.
Scalability: The system should be designed to handle a large user base and increasing data volume without sacrificing performance. Efficient algorithms and infrastructure should be in place to accommodate scalability requirements.
Anti-Spoofing Measures: To enhance system performance, effective anti-spoofing techniques should be incorporated to detect and prevent impersonation or spoofing attacks.
Balancing user acceptance and system performance requires a user-centric approach in the design and implementation of behavioral biometric systems. Engaging users, addressing their concerns, ensuring transparency, and continually monitoring and improving system performance are essential for successful adoption and widespread use of behavioral biometrics.
4.4 Techniques to overcome challenges and enhance reliability
To overcome challenges and enhance the reliability of behavioral biometric systems, several techniques and strategies can be implemented [9, 49]. Here are some approaches:
Robust Algorithm Design: Developing robust algorithms that can handle variability, adapt to changing behavior, and effectively differentiate genuine users from impostors is crucial. Advanced machine learning techniques, such as deep learning and ensemble methods, can be employed to capture complex behavioral patterns and improve recognition accuracy.
Data Augmentation and Diversity: Increasing the diversity and size of the training datasets can help improve the performance and generalization capabilities of behavioral biometric systems. Data augmentation techniques, such as adding noise, perturbations, or variations, can artificially increase the dataset size and introduce more realistic variations in behavior.
Anti-Spoofing Techniques: Implementing effective anti-spoofing measures is essential to counteract spoofing attacks and ensure the integrity of the behavioral biometric system. Various techniques can be employed, such as analyzing user-device interactions, utilizing additional sensors (e.g., touch pressure sensors), and incorporating liveness detection mechanisms.
Continuous Authentication and Adaptive Models: Implementing continuous authentication, where behavior is continuously monitored during user sessions, can enhance system reliability. Adaptive models can be employed to update and refine user profiles in real-time, accommodating changes in behavior over time and improving system performance.
Multi-Modal Fusion: Combining multiple behavioral biometric modalities or fusing behavioral biometrics with other biometric modalities (e.g., combining keystroke dynamics with mouse dynamics) can improve the reliability and accuracy of the system. Multi-modal fusion leverages the strengths of different modalities to compensate for weaknesses and enhance overall performance.
User-Centric Design and Feedback: Involving users in the design process and incorporating user feedback can help identify usability issues, improve system performance, and enhance user acceptance. User-centric design principles, usability studies, and user testing can uncover potential challenges and enable iterative improvements to the system.
By implementing these techniques and strategies, behavioral biometric systems can overcome challenges, enhance reliability, and achieve higher levels of accuracy, usability, and security. Continuous monitoring, evaluation, and improvement are necessary to adapt to evolving threats and ensure the ongoing reliability of the system.
5. Fusion techniques
Fusion techniques play a crucial role in integrating multiple biometric modalities to enhance the accuracy, robustness, and security of biometric systems [10]. Biometric fusion involves combining information from multiple biometric sources to make more reliable and confident decisions about an individual’s identity [50, 51]. By leveraging the strengths of different biometric modalities, fusion techniques aim to overcome the limitations and challenges associated with using a single biometric trait.
The integration of multiple biometric modalities offers several advantages. It can improve recognition accuracy by reducing false acceptances and rejections, enhance system robustness by mitigating the vulnerabilities of individual modalities, and enable more comprehensive and reliable authentication [52]. Fusion techniques can be categorized into two main approaches: feature-level fusion and decision-level fusion.
Feature-level Fusion: Feature-level fusion involves combining the extracted features from different biometric modalities into a unified representation [53]. This technique aims to create a more discriminative and informative feature vector that captures the complementary information from each modality. Various feature-level fusion techniques include:
Concatenation: Features from different modalities are concatenated to create a larger feature vector.
Weighted Fusion: Features are weighted based on their relevance or importance and combined accordingly.
Subspace-based Fusion: Features are transformed into a common subspace where they can be fused using mathematical operations like averaging or linear combination.
Decision-level Fusion: Decision-level fusion involves combining the individual decisions or scores obtained from each biometric modality to make a final authentication decision [54]. This technique focuses on combining the decisions or scores at the decision-making stage. Common decision-level fusion techniques include:
Voting: The decisions or scores from different modalities are aggregated using voting rules such as majority voting, weighted voting, or statistical modeling.
Score-level Fusion: The similarity or matching scores from individual modalities are combined using mathematical operations like averaging, weighted summation, or maximum/minimum selection.
The choice of fusion technique depends on the characteristics of the biometric modalities, the specific application requirements, and the available data. The fusion process may also involve pre-processing steps, such as normalization or alignment, to ensure compatibility between the modalities.
By integrating multiple biometric modalities through fusion techniques, biometric systems can achieve higher accuracy, increased reliability, and improved performance. Fusion enables the utilization of complementary information from different modalities, providing more robust and secure authentication solutions in various domains, including access control, border security, and financial transactions.
5.1 Advantages and limitations of fusion approaches
Fusion approaches in integrating multiple biometric modalities offer several advantages, but they also have certain limitations [55]. Let us explore them in detail:
Advantages of Fusion Approaches:
Improved Accuracy: Fusion techniques leverage the strengths of multiple biometric modalities to enhance recognition accuracy. By combining information from different modalities, fusion can compensate for the limitations and vulnerabilities of individual modalities, resulting in more reliable and accurate authentication decisions.
Robustness and Security: Fusion approaches enhance system robustness by reducing the impact of noise, variability, and spoofing attacks. The combination of multiple modalities makes it harder for attackers to deceive the system or manipulate the authentication process. Fusion also enhances system security by reducing false acceptances and rejections, making it more difficult for unauthorized individuals to gain access.
Complementary Information: Different biometric modalities capture unique and complementary information about an individual’s characteristics. By fusing these modalities, the system can utilize a broader range of information, leading to a more comprehensive representation of the user’s identity. This enables a more robust and reliable authentication process, especially in scenarios where individual modalities may not provide sufficient discriminatory power.
Limitations of Fusion Approaches:
Increased Complexity: Fusion techniques can introduce additional complexity to the system design, implementation, and maintenance. Integration of multiple modalities requires careful consideration of data collection, feature extraction, fusion algorithms, and decision-making processes. The complexity can make system development and deployment more challenging, requiring expertise and resources.
Data Availability and Compatibility: Fusion approaches rely on the availability of data from multiple biometric modalities. Obtaining sufficient and compatible data for each modality can be challenging, especially when dealing with emerging or less common modalities. Data collection protocols, device compatibility, and data quality can significantly impact the effectiveness of fusion techniques.
Performance Degradation: While fusion approaches aim to improve accuracy, there can be scenarios where the fusion process leads to performance degradation. For example, if one modality consistently performs poorly or introduces noise, it may negatively impact the overall fusion results. The choice of fusion technique and the relative importance of each modality’s contribution can affect the performance outcomes.
Increased Resource Requirements: Fusion techniques may require additional computational resources, storage capacity, and processing power compared to single-modality systems. The fusion process involves handling multiple datasets, feature extraction, and decision-making, which can increase system resource requirements. This may limit the scalability or real-time performance of the fusion-based biometric systems.
Despite these limitations, fusion approaches remain valuable in addressing the weaknesses of individual biometric modalities and improving the overall performance and reliability of biometric systems. Careful consideration of these advantages and limitations is crucial when choosing and implementing fusion techniques to achieve the desired authentication outcomes in specific applications.
5.2 Interoperability and compatibility among different modalities
Interoperability and compatibility among different biometric modalities are critical challenges in fusion techniques [10]. Biometric systems often involve integrating multiple modalities, such as face recognition, fingerprint recognition, and iris recognition. Ensuring that these modalities can work together seamlessly and produce consistent results is essential for effective fusion [34]. Here are some key aspects related to interoperability and compatibility in fusion techniques:
Data Representation: Different biometric modalities may employ different data representations and formats. For example, face recognition systems may use image data, while fingerprint recognition systems may utilize minutiae points. To achieve interoperability, it is important to standardize the representation of biometric data, ensuring that the data from different modalities can be easily compared and combined.
Feature Extraction and Matching: Biometric modalities often have distinct feature extraction and matching algorithms. These algorithms may produce different types of features or similarity scores, making it challenging to directly compare them. Fusion techniques need to address these differences by either standardizing the feature extraction methods or designing fusion approaches that can handle diverse feature representations and matching scores.
Template Generation and Storage: Biometric systems typically generate templates from the enrolled biometric data, which are used for matching and verification. These templates may have different formats or structures across modalities. To achieve compatibility, fusion techniques should consider the development of common template formats or translation methods to convert templates between modalities.
Sensor Integration: Biometric modalities often rely on different types of sensors, such as cameras, fingerprint scanners, or iris scanners. Ensuring compatibility at the sensor level is crucial for seamless integration. Sensor interoperability can be achieved through standardized communication protocols, sensor calibration methods, or the use of common sensor technologies.
Standards and Protocols: The establishment of standards and protocols plays a vital role in promoting interoperability and compatibility among biometric modalities. Organizations such as the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST) work towards developing and maintaining standards that facilitate cross-platform and cross-vendor compatibility.
Addressing interoperability and compatibility challenges requires collaboration among researchers, system developers, and standardization bodies. The development of common data formats, standardization of feature representations and matching scores, and adherence to established protocols can greatly enhance the interoperability and compatibility among different biometric modalities, enabling seamless fusion and integration in biometric systems.
5.3 Scalability for large-scale deployment and efficient system performance
Scalability for large-scale deployment and efficient system performance is a crucial consideration in biometric systems [56]. As biometric systems are deployed in various applications and environments, they need to handle a growing number of users while maintaining high performance [34]. Here are some key aspects related to scalability and system performance in biometric systems:
Database Management: As the number of enrolled users increases, the management of biometric databases becomes more challenging. Efficient indexing and retrieval mechanisms need to be implemented to handle large-scale databases effectively. Technologies such as indexing structures, distributed databases, and caching mechanisms can be employed to optimize database management and reduce search times.
Computational Efficiency: Biometric systems need to process and match biometric data in real-time or near real-time. Efficient algorithms and optimization techniques should be employed to ensure fast and accurate processing. This includes optimizing feature extraction, matching algorithms, and fusion techniques to minimize computational complexity and achieve efficient system performance.
Parallel Processing: Large-scale biometric systems can benefit from parallel processing techniques to enhance scalability and speed. Distributed computing architectures, such as clusters or cloud-based infrastructures, can be utilized to distribute the processing load across multiple nodes or servers, enabling faster and more efficient biometric processing.
Hardware Acceleration: The use of specialized hardware, such as graphics processing units (GPUs) or field-programmable gate arrays (FPGAs), can significantly improve system performance and scalability. These hardware accelerators can be leveraged to offload computationally intensive tasks, such as feature extraction or matching, resulting in faster processing times and increased scalability.
System Architecture: Scalable system architectures are essential for accommodating large user populations. Modular and distributed architectures that can handle increased load and allow for easy scalability should be adopted. Load balancing mechanisms and fault-tolerant designs should be implemented to ensure high availability and reliability in large-scale deployments.
Network Bandwidth: In distributed biometric systems, efficient utilization of network bandwidth is crucial. Techniques such as data compression, data reduction, or intelligent data transmission protocols should be employed to minimize the amount of data transferred between different system components, optimizing network bandwidth usage and enhancing scalability.
Efficient scalability and system performance require a combination of algorithmic optimization, hardware acceleration, network optimization, and well-designed system architectures. Continuous monitoring, testing, and optimization are key to ensuring that the biometric system can handle increasing user populations and deliver reliable and efficient performance in real-world deployments.
6. Privacy and security considerations
Biometric authentication systems offer enhanced security and convenience, but they also raise significant privacy concerns [57, 58]. Here is a discussion on some of the key privacy concerns associated with biometric authentication systems:
Biometric Data Protection: The primary privacy concern revolves around the protection of biometric data itself. Biometric data, such as fingerprints, iris patterns, or facial images, is unique to individuals and can potentially reveal sensitive personal information. There is a risk of unauthorized access, misuse, or theft of biometric data, which can lead to identity theft or impersonation.
Centralized Databases: Biometric authentication systems often rely on centralized databases to store and match biometric data. The creation of such databases raises concerns about the security and privacy of the stored data. Unauthorized access to these databases can compromise the privacy of individuals on a large scale.
Data Breaches and Hacking: Like any digital system, biometric authentication systems are susceptible to data breaches and hacking attempts. If biometric data is compromised, individuals may face long-lasting consequences as biometric characteristics are not easily replaceable. The loss or theft of biometric data can have severe privacy implications for affected individuals.
Function Creep and Surveillance: There is a risk of function creep, where initially collected biometric data for authentication purposes may be used for other purposes without individuals’ consent or knowledge. Biometric data, when combined with other data sources, can enable extensive surveillance and tracking, infringing upon individuals’ privacy and civil liberties.
Consent and Control: Biometric authentication systems raise questions about individuals’ consent and control over their biometric data. Users may not have full control over how their data is collected, stored, and used by service providers or third parties. Clear consent mechanisms and transparent privacy policies are essential to ensure individuals’ informed choices and control over their biometric information.
6.1 Techniques for protecting biometric data
To protect biometric data and address privacy concerns, several techniques can be employed [57, 59, 60]. Here are some commonly used techniques for protecting biometric data:
Encryption: Biometric data should be encrypted both at rest and in transit. Encryption techniques, such as symmetric or asymmetric encryption algorithms, can be used to secure the data. Encryption ensures that even if unauthorized access occurs, the data remains unreadable and unusable.
Secure Storage: Biometric data should be stored in secure environments, such as highly protected servers or hardware security modules. Access to the storage should be restricted to authorized personnel only. Additionally, strong access controls, such as multi-factor authentication and role-based access, should be implemented to prevent unauthorized access.
Biometric Template Protection: Instead of storing raw biometric data, biometric systems often store templates derived from the data. Template protection techniques, such as fuzzy commitment, cancelable biometrics, or biometric cryptosystems, can be employed to secure the templates. These techniques ensure that even if the templates are compromised, the original biometric data cannot be reconstructed.
Secure Transmission: When biometric data is transmitted between devices or over networks, secure communication protocols, such as Transport Layer Security (TLS), should be used. Secure transmission prevents unauthorized interception or tampering of the data during transit.
Data Minimization: It is recommended to minimize the collection and storage of biometric data to the extent necessary for authentication purposes. Only essential biometric features required for identification or verification should be captured and stored, reducing the overall risk associated with data storage.
Strong Authentication and Access Controls: To protect biometric data, robust authentication mechanisms should be implemented to ensure that only authorized individuals can access the data. This includes the use of strong passwords, multi-factor authentication, and biometric-based authentication for accessing biometric databases or systems.
Regular System Auditing and Monitoring: Continuous monitoring and auditing of the biometric system help identify any potential vulnerabilities or unauthorized activities. System logs and audit trails should be maintained to track access, modifications, and usage of biometric data. Anomalies or suspicious activities should be promptly detected and investigated.
By implementing these techniques, organizations can significantly enhance the protection of biometric data and address privacy concerns associated with biometric authentication systems. It is crucial to adopt a comprehensive approach that combines technical safeguards, secure practices, and adherence to privacy regulations to ensure the privacy and security of biometric data.
6.2 Biometric encryption, securing biometric data during transmission and storage
Biometric encryption is a technique used to secure biometric data during transmission and storage. It involves applying cryptographic algorithms and protocols to protect the confidentiality, integrity, and authenticity of biometric information [61, 62, 63]. The primary goal of biometric encryption is to ensure that the biometric data remains secure and cannot be accessed or tampered with by unauthorized parties. Here’s an explanation of how biometric encryption works:
Encryption during Transmission:
Secure Communication Protocols: Biometric data is encrypted using secure communication protocols, such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), when transmitted over networks or between devices. These protocols establish a secure channel for data exchange, preventing unauthorized interception or tampering of the biometric data in transit.
Encryption Algorithms: Biometric data can be encrypted using strong encryption algorithms, such as Advanced Encryption Standard (AES), to transform the data into ciphertext. The encryption process ensures that even if the transmitted data is intercepted, it remains unreadable and unintelligible to unauthorized entities [64].
Key Exchange: To facilitate secure communication, encryption requires the exchange of cryptographic keys between the sender and receiver. The keys are used to encrypt and decrypt the biometric data. Secure key exchange protocols, such as Diffie-Hellman key exchange, are utilized to establish a shared secret key without revealing it to eavesdroppers [65].
Encryption during Storage:
Data-at-Rest Encryption: Biometric data stored in databases or on storage media should be protected using data-at-rest encryption. This involves encrypting the data using encryption algorithms before it is stored. Encrypted data remains unreadable and unusable unless decrypted with the appropriate cryptographic keys.
Key Management: Proper key management is crucial for the security of encrypted biometric data. The encryption keys should be securely stored, and access to the keys should be restricted to authorized personnel only. Key rotation, periodic key updates, and secure key storage mechanisms, such as Hardware Security Modules (HSMs), can be employed to enhance key management.
Authentication and Integrity Verification [66]:
Digital Signatures: Digital signatures can be used to verify the authenticity and integrity of biometric data. A digital signature is created using the sender’s private key and can be verified using the sender’s public key. By attaching a digital signature to the encrypted biometric data, the receiver can verify that the data has not been tampered with during transmission.
Message Authentication Codes (MAC): MAC algorithms can be employed to ensure the integrity of the biometric data. A MAC is generated by applying a secret key to the data, creating a unique tag that can be verified by the receiver. If the data is tampered with, the MAC verification will fail, indicating potential unauthorized modification.
Access Control and Authorization:
Role-Based Access Control (RBAC): Access to encrypted biometric data should be controlled based on the roles and privileges of the users. RBAC ensures that only authorized individuals with the necessary permissions can access and decrypt the biometric data.
Two-Factor Authentication (2FA): Adding an additional layer of authentication, such as requiring a second factor (e.g., a password or a token), strengthens the security of encrypted biometric data. 2FA ensures that even if the cryptographic keys are compromised, an additional authentication factor is required to access the data.
Biometric encryption plays a crucial role in safeguarding biometric data during transmission and storage. By employing strong encryption algorithms, secure communication protocols, and proper key management practices, biometric systems can enhance the security and privacy of individuals’ biometric information, mitigating the risks associated with unauthorized access, interception, or tampering of the data.
6.3 Spoofing attacks and presentation attacks prevention techniques
Spoofing attacks, also known as presentation attacks or biometric spoofing, are attempts to deceive a biometric authentication system by presenting fake or altered biometric traits to impersonate another individual [67, 68, 69, 70]. These attacks pose a significant security threat to biometric systems. To prevent spoofing attacks, various techniques and countermeasures can be implemented. Here are some commonly used prevention techniques:
Liveness Detection: Liveness detection is a technique used to verify that the presented biometric trait is from a live and genuine source, rather than a fake or replayed sample. It involves capturing additional data or performing specific actions to ensure the presence of vital signs or human characteristics. For example, in facial recognition, liveness detection can involve analyzing facial movements or requesting the user to perform specific actions like blinking or smiling.
Physiological and Behavioral Anti-Spoofing Techniques: These techniques aim to detect and differentiate between genuine biometric traits and fake or synthetic ones. Physiological anti-spoofing techniques analyze physiological properties of the biometric trait, such as blood flow, temperature, or texture, to determine its authenticity. Behavioral anti-spoofing techniques analyze behavioral patterns or dynamics associated with the biometric trait, such as the movement of facial muscles or typing dynamics, to detect spoofing attempts.
Multimodal Biometrics: Using multiple biometric modalities simultaneously, such as combining fingerprint and iris recognition, can enhance security by increasing the difficulty of spoofing. By requiring multiple genuine biometric traits for authentication, the risk of successful spoofing attacks is significantly reduced.
Fusion of Biometric and Non-Biometric Data: Combining biometric data with non-biometric data, such as user-specific information or contextual data, can strengthen the security of the authentication process. For example, incorporating device information, location data, or user behavior patterns into the authentication decision can help detect and prevent spoofing attacks.
Challenge-Response Mechanisms: Implementing challenge-response mechanisms adds an extra layer of security to the authentication process. The system can generate random challenges or request specific actions from the user that are difficult to replicate in a spoofing attempt. The user’s response is then validated to ensure authenticity.
By implementing a combination of these prevention techniques, biometric systems can significantly reduce the risk of spoofing attacks and enhance the overall security and reliability of the authentication process. Continuous research and development in anti-spoofing techniques are essential to stay ahead of evolving spoofing techniques and ensure the effectiveness of countermeasures.
7. Conclusion
This chapter explores various biometric modalities, their advancements, integration challenges, and techniques to enhance security and usability. Here is a summary of the key findings discussed in the chapter:
Iris Recognition: Iris recognition is a reliable and unique biometric modality with high accuracy and stability. Advancements in iris recognition techniques include multi-sensor fusion for enhanced accuracy and robustness, as well as the application of deep learning algorithms for improved iris feature extraction and matching.
Gait Recognition: Gait recognition is a non-intrusive biometric modality that analyzes an individual’s walking pattern. Recent advancements in gait recognition algorithms have focused on deep learning approaches for improved gait analysis and identification.
Behavioral Biometrics: Behavioral biometrics, such as keystroke dynamics, mouse dynamics, and signature dynamics, offer continuous authentication capabilities. These traits can be used to verify and authenticate users based on their unique behavioral patterns.
Challenges in Biometric Recognition: Biometric recognition systems face various challenges, including occlusion in iris recognition, variations due to clothing and footwear in gait recognition, and user acceptance and system performance in behavioral biometrics. These challenges need to be addressed to ensure accurate and reliable recognition.
Techniques to Address Challenges: To overcome challenges and improve recognition accuracy, techniques such as occlusion handling methods, non-cooperative scenario handling techniques, and performance optimization approaches can be employed. These techniques aim to enhance the robustness and usability of biometric authentication systems.
Fusion Techniques: Integration of multiple biometric modalities through score-level fusion or decision-level fusion can enhance recognition accuracy and system reliability. Advantages of fusion approaches include increased discriminative power, improved robustness against spoofing attacks, and enhanced overall system performance. However, fusion techniques also come with limitations such as increased complexity, interoperability issues, and scalability concerns.
By understanding the advancements, challenges, and techniques discussed in this chapter, stakeholders in the field of biometric authentication can gain insights into the latest developments, potential risks, and strategies to enhance the security, usability, and reliability of biometric systems.
7.1 Emphasis on the need for ongoing research and development efforts
The chapter highlights the crucial need for ongoing research and development efforts in the field of biometric authentication. Here are some key reasons for the emphasis on continuous research:
Advancements in Technology: Biometric technologies are constantly evolving, and new modalities, algorithms, and techniques are being developed. Ongoing research ensures that biometric systems keep up with technological advancements and take advantage of the latest innovations. This helps improve the accuracy, efficiency, and reliability of biometric authentication.
Addressing Emerging Challenges: Biometric systems face various challenges, including spoofing attacks, privacy concerns, usability issues, and system vulnerabilities. Ongoing research is essential to understand and address these challenges effectively. It enables the development of robust countermeasures, security techniques, and mitigation strategies to protect against evolving threats.
Enhancing Security and Privacy: As biometric authentication becomes more prevalent, the need for stronger security and privacy measures increases. Ongoing research focuses on developing advanced encryption methods, secure storage and transmission protocols, and techniques to protect biometric data from unauthorized access or misuse. Continuous efforts in research help ensure the highest levels of security and privacy in biometric systems.
Improving User Experience: User experience and acceptance play a crucial role in the adoption of biometric authentication. Ongoing research aims to enhance the usability, convenience, and user-friendliness of biometric systems. This includes exploring novel interaction methods, improving recognition accuracy, reducing false acceptance and rejection rates, and addressing user concerns and preferences. Research efforts strive to make biometric authentication systems more user-centric and user-friendly.
Standardization and Interoperability: Standardization is vital for the interoperability and compatibility of biometric systems across different platforms and organizations. Ongoing research contributes to the development of industry standards, protocols, and guidelines for biometric data exchange, system integration, and interoperability. This ensures seamless integration of biometric technologies and facilitates their widespread adoption.
Future Applications and Innovations: Ongoing research and development efforts pave the way for future applications and innovations in biometric authentication. By pushing the boundaries of technology, researchers can explore new modalities, fusion techniques, and emerging areas such as behavioral biometrics, continuous authentication, or multi-modal systems. This leads to novel use cases, improved system performance, and expanded possibilities for biometric authentication in various domains [11, 14, 71].
In summary, ongoing research and development efforts are essential to drive advancements, address challenges, enhance security and privacy, improve user experience, foster interoperability, and unlock the full potential of biometric authentication systems. The field of biometrics relies on continuous innovation and research to stay at the forefront of secure and reliable authentication technologies.
7.2 Importance of considering privacy, security, and usability aspects in designing biometric authentication systems
Considering privacy, security, and usability aspects is of utmost importance in designing biometric authentication systems. Here are the key reasons why these aspects should be carefully addressed:
Privacy Protection: Biometric data is highly sensitive and personal, as it uniquely identifies individuals. Designing systems with strong privacy protections ensures that users’ biometric information is handled in a secure and confidential manner. Privacy-enhancing techniques, such as data anonymization, secure storage, and secure transmission protocols, should be implemented to prevent unauthorized access, data breaches, or misuse of biometric data.
Security Enhancement: Biometric authentication systems must be designed with robust security measures to protect against attacks, fraud, and unauthorized access. Biometric data is irreplaceable, and if compromised, it can lead to severe consequences. Incorporating strong encryption algorithms, access controls, multi-factor authentication, and anti-spoofing techniques helps ensure the integrity and confidentiality of biometric information. Regular security audits, vulnerability assessments, and adherence to security best practices are essential for maintaining system security.
Usability and User Acceptance: Biometric systems should prioritize usability to ensure a positive user experience and encourage widespread adoption. Complex enrollment processes, lengthy verification procedures, or frequent false rejections can hinder user acceptance. Designing intuitive user interfaces, optimizing recognition accuracy, minimizing enrollment efforts, and providing clear user instructions contribute to system usability. User feedback and usability testing play a crucial role in refining the design and making the system user-friendly.
Trust and Confidence: Privacy, security, and usability aspects are fundamental for establishing trust and confidence among users and stakeholders. Individuals must have confidence that their biometric data is being handled securely and with utmost care. Trust in the system’s reliability, accuracy, and privacy safeguards is vital for user acceptance and long-term adoption of biometric authentication technologies.
Compliance with Regulations: Many jurisdictions have specific regulations and laws governing the collection, storage, and use of biometric data. Designing biometric authentication systems with privacy, security, and usability considerations ensures compliance with these regulations, minimizing legal risks and potential penalties.
By considering privacy, security, and usability aspects throughout the design and implementation of biometric authentication systems, organizations can build trust, protect individual privacy, enhance security, and promote user acceptance. It is essential to strike a balance between these aspects to develop robust, user-friendly, and ethically sound biometric authentication systems that meet the needs of individuals and organizations alike.
7.3 Closing remarks on the future potential of emerging biometric modalities and integration challenges
In conclusion, the future potential of emerging biometric modalities and the integration challenges they present are promising and exciting. The advancements in technologies such as iris recognition, gait recognition, and behavioral biometrics offer new avenues for secure and convenient authentication systems. However, it is essential to address the integration challenges and overcome the associated hurdles to fully realize their potential.
By continuing research and development efforts, researchers and practitioners can enhance the accuracy, robustness, and usability of biometric authentication systems. Fusion techniques that integrate multiple modalities can further improve recognition accuracy and system reliability. Moreover, the ongoing focus on privacy, security, and usability aspects ensures that biometric systems are designed with the highest ethical standards and user-centric considerations.
As emerging biometric modalities become more prevalent, the future holds exciting possibilities for their application in various domains. From enhancing security in critical infrastructures to enabling seamless user experiences in everyday interactions, biometric authentication has the potential to transform the way we interact with technology. However, it is crucial to remain mindful of the challenges that arise with the integration of multiple modalities, interoperability issues, scalability concerns, and the need for continuous advancements to address emerging threats. By proactively addressing these challenges, researchers and practitioners can create robust, reliable, and user-friendly biometric authentication systems that meet the evolving needs of individuals and organizations.
Overall, the future of emerging biometric modalities and integration challenges is bright, and with ongoing research, innovation, and collaboration, we can unlock the full potential of biometric authentication, ensuring a secure and convenient authentication landscape for the years to come.
References
- 1.
Pato JN, Millett LI. Biometric Recognition: Challenges and Opportunities. National Research Council (US) Whither Biometrics Committee. Washington (DC): National Academies Press (US); 2010. PMID: 25032357 - 2.
Jain AK, Nandakumar K, Ross A. 50 years of biometric research: Accomplishments, challenges, and opportunities. Pattern Recognition Letters. 2016; 79 :80-105 - 3.
Tiwari S, Singh SK. Face recognition for newborns. Dhanbad, India: IET Biometrics. 2012; 1 (4):200-208. DOI: 10.1049/iet-bmt.2012.0040. ISSN: 2047-4946. [IF-2.716] - 4.
Tiwari S, Singh SK. Newborn verification using headprint. Journal of Information Technology Research (JITR), Vol. 5, No. 2, pp. 15-30, 2012. DOI: 10.4018/jitr.2012040102, ISSN: 1938-7857. (IGI Global). [Thomson Reuters, Scopus] [IF-0.9] - 5.
Tiwari S, Singh A, Singh SK. Intelligent method for face recognition of infant. International Journal of Computer Applications. 2012; 52 (4):36-50. DOI: 10.5120/8194-1569, ISSN: 0975-8887 - 6.
Tiwari S, Singh A, Singh SK. Can ear and soft-biometric traits assist in recognition of newborn? In: Proceedings of International Conference on Computer Science, Engineering and Applications. New Delhi, India: Springer Berlin Heidelberg; 2012. pp. 179-192. DOI: 10.1007/978-3-642-30157-5, ISBN: 978-3-642-30157-5 - 7.
Tiwari S, Singh A, Singh SK. Can face and soft-biometric traits assist in recognition of newborn? In: Proceedings of IEEE, International Conference on Recent Advanced in Information Technology, IEEE Catalog Number: CFP1234P-ART, ISBN: 978-1-4577-0694-3. Dhanbad, India: ISM; 2012. pp. 74-79 - 8.
Tiwari S, Singh SK. Information security governance using biometrics. In: Mellado D et al., editors. IT Security Governance Innovations: Theory and Research. Spain: IGI Global Publishing; 2012, Chapter 8. ISBN: 9781466620834. DOI: 10.4018/978-1-4666-2083-4.ch008 - 9.
Jain AK, Ross A, Pankanti S. Biometrics: A tool for information security. IEEE Transactions on Information Forensics and Security. 2006; 1 (2):125-143 - 10.
Ross AA, Nandakumar K, Jain AK. Handbook of Multibiometrics. Vol. 6. Michigan State University, USA Patrick Flynn: Springer Science & Business Media; 2006 - 11.
Raja R, Raja H, Patra RK, Mehta K, Akanksha G, Ramya Laxmi K. Assessment methods of cognitive ability of human brains for inborn intelligence potential using pattern recognition. In: Biometric Systems. London, UK: IntechOpen; 2021; ISBN 978-1-78984-188-6 - 12.
Raja R, Raja H, Dubey P, Ingle D. Information Systems Management. London, United Kingdom: IntechOpen; 2023 - 13.
Raja R, Sharma PC, Mahmood MR, Saini DK. Analysis of anomaly detection in surveillance video: Recent trends and future vision. Multimedia Tools and Applications. 2023; 82 :12635-12651. DOI: 10.1007/s11042-022-13954-1 - 14.
Raja R, Kumar S, Choudhary S, Dalmia H. An effective contour detection based image retrieval using multi-fusion method and neural network. Wireless Personal Communication. 2021; 1 :1-21. PREPRINT (Version 2). DOI: 10.21203/rs.3.rs-458104/v1. Available at Research Square - 15.
Tiwari S, Singh SK. Does all newborn face lookalike to human and machine? Proceedings of the National Academy of Sciences, India Section A: Physical Sciences. 2015; 5 (17):211-220. DOI: 10.1007/s40010-014-0196-7. (Springer). ISSN: 0369-8203. [IF-0.9] - 16.
Kumar S, Raja R, Tiwari S, Rani S. Cognitive Behavior & Human Computer Interaction Based on Machine Learning Algorithm. London, United Kingdom: Wiley & Scrivener Publishing; 2021. ISBN No: 13:9781119791607 - 17.
Tiwari S, Jain S, Chandel SS, Kumar S, Kumar S. Comparison of adult and newborn ear images for biometric recognition. In: Proceedings of IEEE, Fourth International Conference on —Parallel Distributed and Grid Computing (PDGC), 22nd-24th, 2016. Solan, Shimla, India: JUIT; 2016. pp. 421-426. Conference ID: 38036, ISBN: 978-1-5090-3668-4. DOI: 10.1109/PDGC.2016.7913232 - 18.
Mahmood R, Raja R, Kumar S, Nagwanshi K. Ambient Intelligence and Internet of Things: Convergent Technologies. Beverly, MA: Scrivener Publishing-Wiley; 2022. ISBN: 9781119821236 - 19.
Abuhamad M, Abusnaina A, Nyang D, Mohaisen D. Sensor-based continuous authentication of smartphones’ users using behavioral biometrics: A contemporary survey. IEEE Internet of Things Journal. 2020; 8 (1):65-84 - 20.
Janghel RR, Raja R, Cengiz K. Next Generation Healthcare Systems Using Soft Computing Techniques. USA: CRC Press; 2022. ISBN: 9781032107974 - 21.
Daugman J. The importance of being random: Statistical principles of iris recognition. Pattern Recognition. 2003; 36 (2):279-291 - 22.
Ma L, Tan T, Wang Y, Zhang D. Personal identification based on iris texture analysis. IEEE Transactions on Pattern Analysis and Machine Intelligence. 2003; 25 (12):1519-1533 - 23.
Wildes RP, Asmuth JC, Green GL, Hsu SC, Kolczynski RJ, Matey JR, etal. A system for automated iris recognition. In Proceedings of 1994 IEEE Workshop on Applications of Computer Vision. FL, USA: IEEE; 1994. pp. 121-128 - 24.
Blum RS, Liu Z, editors. Multi-Sensor Image Fusion and its Applications. Boca Raton: CRC Press; 2018 - 25.
Bowyer KW, Hollingsworth K, Flynn PJ. Image understanding for iris biometrics: A survey. Computer Vision and Image Understanding. 2008; 110 (2):281-307 - 26.
Maltoni D, Maio D, Jain AK, Prabhakar S. Handbook of Fingerprint Recognition. Vol. 2. London: Springer; 2009 - 27.
Tiwari S, Singh A, Singh RS, Singh SK. Internet security using biometrics. In: Vidyarthi DP, editor. Technologies and Protocols for Future Internet Design: Reinventing in Web. India: IGI Global Publishing; 2011. Chapter 6. ISBN: 9781466602038. DOI: 10.4018/978-1-4666-0203-8.ch006 - 28.
Gravina R, Alinia P, Ghasemzadeh H, Fortino G. Multi-sensor fusion in body sensor networks: State-of-the-art and research challenges. Information Fusion. 2017; 35 :68-80 - 29.
Chandrakar R, Raja R, Miri R. Animal detection based on deep convolutional neural networks with genetic segmentation. Multimedia Tools and Applications. 2021; 81 :42149-42162. DOI: 10.1007/s11042-021-11290-4 - 30.
Tiwari S, Kumar S, Singh SK, Singh A. Newborn recognition using multimodal biometric. In: Encyclopedia of Information Science and Technology. 3rd ed. USA: Mehdi Khosrow-Pour Information Resources Management Association; 2014. pp. 4347-4357. DOI: 10.4018/978-1-4666-5888-2. ISBN: 9781466658882. ch427 - 31.
Kumar S, Rohit Raja M, Mahmood R, Choudhary S. A hybrid method for the removal of RVIN using self organizing migration with adaptive dual threshold median filter. Sensing and Imaging Springer Journal. 2023; 24 :9. DOI: 10.1007/s11220-023-00414-9 - 32.
Nguyen K, Fookes C, Ross A, Sridharan S. Iris recognition with off-the-shelf CNN features: A deep learning perspective. IEEE Access. 2017; 6 :18848-18855 - 33.
Tiwari S, Singh SK. Multimodal biometric recognition for newborn. In: Srivastava R, Singh SK, Shukla KK, editors. Research Developments in Biometrics and Video Processing Techniques. India: IGI Global Publishing; 2013. Chapter 2. ISSN: 1948-9730, ISBN: 9781466648685 - 34.
Jain AK, Kumar A. Biometrics of next generation: An overview. Second Generation Biometrics. 2010; 12 (1):2-3 - 35.
Pandey S, Miri R, Sinha GR, Raja R. AFD filter and E2n2 classifier for improving visualization of crop image and crop classification in remote sensing image. International Journal of Remote Sensing. 2022; 43 (1):5848-5873. DOI: 10.1080/01431161.2021.2000062 - 36.
Dehzangi O, Taherisadr M, ChangalVala R. IMU-based gait recognition using convolutional neural networks and multi-sensor fusion. Sensors. 2017; 17 (12):2735 - 37.
Sepas-Moghaddam A, Etemad A. Deep gait recognition: A survey. IEEE Transactions on Pattern Analysis and Machine Intelligence. 2022; 45 (1):264-284 - 38.
Tunca C, Salur G, Ersoy C. Deep learning for fall risk assessment with inertial sensors: Utilizing domain knowledge in spatio-temporal gait parameters. IEEE Journal of Biomedical and Health Informatics. 2019; 24 (7):1994-2005 - 39.
Unar JA, Seng WC, Abbasi A. A review of biometric technology along with trends and prospects. Pattern Recognition. 2014; 47 (8):2673-2688 - 40.
Gafurov D. A survey of biometric gait recognition: Approaches, security and challenges. In: Annual Norwegian Computer Science Conference. Norway: Annual Norwegian Computer Science Conference; 2007. pp. 19-21 - 41.
Traore I, Alshahrani M, Obaidat MS. State of the art and perspectives on traditional and emerging biometrics: A survey. Security and Privacy. 2018; 1 (6):e44 - 42.
Alsultan A, Warwick K. Keystroke dynamics authentication: A survey of free-text methods. International Journal of Computer Science Issues (IJCSI). 2013; 10 (4):1 - 43.
Wang L, Geng X, editors. Behavioral Biometrics for Human Identification: Intelligent Applications: Intelligent Applications. IGI Global; 2009 - 44.
Jorgensen Z, Yu T. On mouse dynamics as a behavioral biometric for authentication. In: Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security. Melbourne VIC Australia; 2011. pp. 476-482 - 45.
Patel VM, Chellappa R, Chandra D, Barbello B. Continuous user authentication on mobile devices: Recent progress and remaining challenges. IEEE Signal Processing Magazine. 2016; 33 (4):49-61 - 46.
Sharma PC, Raja R, Vishwakarma SK, Sharma S. Analysis of brain signal processing and real-time EEG signal enhancement. Multimedia Tools and Applications. 2022; 81 :1-21. DOI: 10.1007/s11042-022-12887-z - 47.
El-Abed M, Giot R, Hemery B, Rosenberger C. A study of users’ acceptance and satisfaction of biometric systems. In: 44th Annual 2010 IEEE International Carnahan Conference on Security Technology. San Jose, CA, USA: IEEE; 2010. pp. 170-178 - 48.
Zhang D. Automated Biometrics: Technnologies and Systems. New york: Springer Science & Business Media; 2000 - 49.
Yampolskiy RV, Govindaraju V. Behavioural biometrics: A survey and classification. International Journal of Biometrics. 2008; 1 (1):81-113 - 50.
Jain AK, Ross A, Prabhakar S. An introduction to biometric recognition. IEEE Transactions on Circuits and Systems for Video Technology. 2004; 14 (1):4-20 - 51.
Jain AK, Pankanti S, Prabhakar S, Hong L, Ross A. Biometrics: A grand challenge. In: Proceedings of the 17th International Conference on Pattern Recognition. Vol. 2. Michigan State University: IEEE; 2004. pp. 935-942 - 52.
Ortega-Garcia J, Bigun J, Reynolds D, Gonzalez-Rodriguez J. Authentication gets personal with biometrics. IEEE Signal Processing Magazine. 2004; 21 (2):50-62 - 53.
Xin Y, Kong L, Liu Z, Wang C, Zhu H, Gao M, et al. Multimodal feature-level fusion for biometrics identification system on IoMT platform. IEEE Access. 2018; 6 :21418-21426 - 54.
Chatzis V, Bors AG, Pitas I. Multimodal decision-level fusion for person authentication. IEEE Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans. 1999; 29 (6):674-680 - 55.
Sahoo SK, Choubisa T, Prasanna SM. Multimodal biometric person authentication: A review. IETE Technical Review. 2012; 29 (1):54-75 - 56.
Shaikh SA, Rabaiotti JR. Characteristic trade-offs in designing large-scale biometric-based identity management systems. Journal of Network and Computer Applications. 2010; 33 (3):342-351 - 57.
Prabhakar S, Pankanti S, Jain AK. Biometric recognition: Security and privacy concerns. IEEE Security & Privacy. 2003; 1 (2):33-42 - 58.
Rui Z, Yan Z. A survey on biometric authentication: Toward secure and privacy-preserving identification. IEEE Access. 2018; 7 :5994-6009 - 59.
Akhtar Z, Hadid A, Nixon MS, Tistarelli M, Dugelay JL, Marcel S. Biometrics: In search of identity and security (Q & A). IEEE Multimedia. 2018; 25 (3):22-35 - 60.
Jain AK, Ross A, Uludag U. Biometric template security: Challenges and solutions. In: 2005 13th European Signal Processing Conference. Antalya, Turkey: IEEE; 2005. pp. 1-4 - 61.
Cherukuri S, Venkatasubramanian KK, Gupta SK. Biosec: A biometric based approach for securing communication in wireless networks of biosensors implanted in the human body. In: 2003 International Conference on Parallel Processing Workshops. Kaohsiung, Taiwan: IEEE; 2003. pp. 432-439 - 62.
Kaur H, Khanna P. Biometric template protection using cancelable biometrics and visual cryptography techniques. Multimedia Tools and Applications. 2016; 75 :16333-16361 - 63.
Kumar S, Singh SK, Singh AK, Tiwari S, Singh RS. Privacy preserving security using biometrics in cloud computing. Multimedia Tools and Applications. 2018; 77 :11017-11039 - 64.
Raja R, Nagwanshi KK, Sandeep Kumar K, Laxmi R. Data Mining Technologies Using Machine Learning Algorithms. Beverly, MA: Wiley & Scrivener Publishing; 2022. ISBN No: 13:9781119791782 - 65.
Kumar S, Raja R, Kushwaha AKS, Kumar S, Patra RK. Green Computing and its Applications. NY, USA: Nova Science Publication; 2022. DOI: 10.52305/ENYH6923. ISBN: 978-1-68507-357-2 - 66.
Chandrakar R, Raja R, Miri R, Patra RK, Sinha U. Computer succored vaticination of multi-object detection and histogram enhancement in low vision. International Journal of Biometrics. Special Issue: Investigation of Robustness in Image Enhancement and Preprocessing Techniques for Biometrics and Computer Vision Applications. 2023; 15 (3-4):255-271. DOI: 10.1504/IJBM.2023.130671 - 67.
Roberts C. Biometric attack vectors and defences. Computers & Security. 2007; 26 (1):14-25 - 68.
Raja R, Gupta D, Varshney N, Kumar A. Detection of behavioral patterns employing a hybrid approach of computational techniques. Computers, Materials & Continua. 2022; 72 (1):2015-2031 - 69.
Sahu AK, Sharma S, Raja R. Deep learning-based continuous authentication for an IoT-enabled healthcare service. Computers & Electrical Engineering. 2022; 99 :107817. ISSN 0045-7906. DOI: 10.1016/j.compeleceng.2022. 107817 - 70.
Chandrakar R, Raja R, Miri R, Kushwaha A. Enhanced the moving object detection and object tracking for traffic surveillance using RBF-FDLNN and CBF algorithm. Expert Systems with Applications. 2022; 191 :116306. ISSN: 0957-4174. DOI: 10.1016/j.eswa.2021.116306 - 71.
Sahu AK, Suraj Sharma M, Tanveer RR. Internet of things attack detection using hybrid deep learning model. Computer Communications. 2021; 176 :146-154. ISSN 0140-3664. DOI: 10.1016/j.comcom.2021.05.024